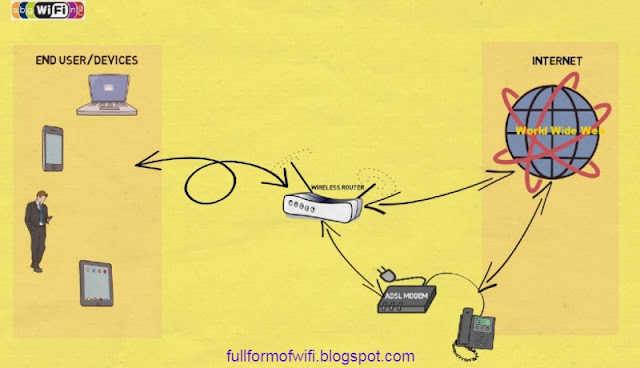
What Is WLAN? WLAN WiFi: When people say WLAN,
they usually mean wireless internet or Wi-Fi or Wi-Fi hotspot. WLAN literally means a wireless local area network. We're
talking about a local area network created by something like this, a wireless
router.
This wireless router will plug into your internet modem and will take
that internet and share it wirelessly through a radio signal with all your
Wi-Fi or WLAN compatible devices, like this
laptop or your phone or your tablet or even your TV.
The network that this
wireless hotspot creates is not as fast as the one you will get with a regular LAN,
which is by connecting it to an Ethernet cable. It is very, very convenient,
and it lets you have internet in places that you would not normally have
internet in or that would be really hard to get internet in.
The nice thing
about wireless LAN is that it enables you to sit on the sofa with your laptop,
not having any cables around and still get the full internet without any speed
issues or limitations. Basically, WLAN is just another way of saying Wi-Fi or
hotspot and that's the way it works.
Now most of us had connected to a Wi-Fi network with our laptop, tablet or even our smartphone, and to join that network with our device you had to select a network name and you had to supply a password. Now Wi-Fi network can be just open with no password required, so that means that anybody can join it.
WEPWEP or Wired Equivalent Privacy:
However, in the majority of cases, Wi-Fi networks will be secure and will require a password. Now there are several different protocols that are used for securing a Wi-Fi network. So let's start with a secure protocol called WEPWEP or Wired Equivalent Privacy was developed in 1999and its the earliest security protocol that was used for wireless networks. And also as its name implies it's meant to supply the same security to wireless networks as it did for wired networks.
However, this turned out not to be the case because after a time it was found out that a 40-bit encryption key that WEP used as vulnerable and not secure. And therefore it was easily hackable. So that's why today WEP is no longer used and modern wi-fi routers won't even have it as an option anymore.
So a better security protocol was needed for wireless networks. And that brings us to WPAWPA or Wi-Fi Protected Access is another wireless security protocol that was developed to solve the problems of WEPWPA is far better than WEP and this is because it uses stronger encryption methods called TKIP which stands for Temporal Key Integrity Protocol. And TKIP dynamically changes its keys as its being used and this ensures data integrity.
But even though WPA is more secure than WEP even today WPA is outdated because TKIP did have some vulnerabilities. And that brings us to WPA2 was developed to provide even stronger security than WPA. And it does this by requiring the use of a stronger encryption method. While WPA uses TKIP for encryption which is known to have some limitationsWPA2 uses AES which stands for Advanced Encryption Standard. AES uses asymmetric encryption algorithms which makes it strong enough to resist a brute-force attack fact AES is so secure that the U.S. federal government has adopted it and is now using it to encrypt sensitive government data.
Wi-Fi routers configuration:
Now when you log into the Wi-Fi routers configuration page you go into the Wi-Fi security section this is where you would find the different security protocols that you can choose from to protect your Wi-Fi network here is an example from an older Linksys router and here you can see the WEP, WPA and WPA2 protocols that we discussed. Now as I said this router is a few years old and it still has WEP as an option.
However, newer routers like this one here won’t even have WEP as an option because WEP is weak and outdated and is no longer used and thank god for that because it was garbage. Now you also noticed that on both of these routers there's an option that has both WPA and WPA2and this is a mixed security option.
This option enables WPA and WPA2 at the same time so it’ll use both TKIP and AES security. Now the reason for this option is for compatibility purposes because some older devices like prior to 2006may not be compatible with using AES encryption that’s used with WPA2and so these older devices will connect to the older WPA protocol but at the same time modern devices will connect to WPA2.
Now some people might ask why not just choose the mixed option all the time since it’s the most compatible with all devices. Well, you can do this but the problem is that in addition to using AES its also using TKIP and since TKIP is not as strong as you're leaving your network more vulnerable to a breach.
However, if all of your devices are modern then the best option is to choose WPA2 which only uses AES. Now the next generation of wireless security is WPA3.WPA3 was introduced in 2018 and according to the official Wi-Fi websitehttps://www.wi-fi.org/WPA3 provides cutting edge security protocols to the market.
It adds new features to simplify Wi-Fi security and enables more robust authentification and it will receive increased protections from password guessing attempts. Now WPA3 won’t be available on every Wi-Fi router that you purchase today because it was just introduced last year. However, you will start to see it more and more on Wi-Fi products in the next few months.
Wi-Fi Protected Setup and WPS:
Now so far we discussed a few password-protected security protocols but there is another wireless security method that doesn’t require you to type in a password and this method is called WPS.WPS stands for Wi-Fi Protected Setup and WPS was designed for people who know little about wireless networks to make it as easy as possible for their devices to join a wireless network.
So, here is a WPS configuration page for our router. And there are a couple of different methods that are used with WPS. But by far the most common method is the push button method.
So, with this method, you would just press a couple of buttons and then you'd be connected. So, for example, most routers today will have a physical WPS button that you can press and a lot of Wi-Fi printers will also have a software or a physical WPS button so let’s say you wanted to connect this wireless printer to your Wi-Fi network so you would press the WPS button on your Wi-Fi router and within 2 minutes you would press the WPS button on your printer and then your printer would connect to the Wi-Fi router in a few seconds.
And that’s really as simple as it gets. And you can also use method two if you want if your client has a WPS pin number. So you would just enter that pin number into the field below and within a few seconds, it’ll connect. So as stated before WPS is the easiest way to join a wireless network and a lot of manufacturers have built their wireless products with WPS. And this is to make it as simple as possible for their costumers to join their device to a wireless network.
Access Controler (MAC Filter):
Now there’s one more method we need to talk about and this is called the Access Controler in some routers it’s called the MAC Filter and with this option, you can either allow or block devices from joining your network.
Every network adapter has a MAC address and is a hexadecimal number that uniquely identifies each device on a network and with Access Control you can either allow or block access by using the device’s MAC address.
When a device is blocked it would only be able to get an IP address from your router but it won’t be able to communicate with any other device and it would not be able to connect to the Internet so the Access Control is just an extra layer of security that’s in addition to your Wi-Fi password and the Access Control is also for wired devices.